Personal DNS Server with PiHole
- Freddy Dopfel
- Apr 4, 2019
- 3 min read
My next step for continuous improvement of my home network was to build a DNS server using the popular DIY-system, PiHole. A DNS server takes web addresses like "facebook.com" and then looks up the server location (something like 76.103.245.57) in an address book, so the computer knows which server to talk to. So why would I want to host this myself, rather than using the default DNS that my ISP (Comcast) provides?
1. Speed: Each request doesn't need to travel up to Comcast's servers (just to a device in my own network), greatly reducing the time for requests.
2. Privacy: Selectively block certain DNS requests to telematics sites, so that my user data cannot be uploaded. Make Comcast's job selling my browsing habits a little bit harder without a DNS log of their own.
3. Analytics: With well over 50 devices on my network, a local DNS will allow me to see to what sites they are reaching out, and how often. This is important to ensure that none of my many IoT devices have been compromised.
4. Ad Blocking: When a website tries to send a request to an ad server like adservice.google.com, my personal DNS server simply says that the server does not exist, so my computer doesn't even begin to download the ad (most ad blockers still download the ad, but then adjust the framework of the web page to hide it). This also blocks ads on other devices where I can't install ad blockers, like smartphones, TVs, etc. Network-wide ad blocking is perhaps the biggest reason to set up your own DNS server.
Setup of PiHole is surprisingly easy. All you have to do is get a Raspberry Pi, format a SD card with Raspbian (a popular Linux-based OS for Raspberry Pi), open the terminal, and type in:
curl -sSL https://install.pi-hole.net | bash
This installs the PiHole software and a community-maintained blacklist of domains that include ad servers and telematics (usage data) servers where personal information is often sent without consent. For addresses that are okay, the PiHole will reach out to existing DNS servers (in this case, I chose Cloudflare and Google DNS). However, for commonly-reached domains, the PiHole caches these addresses locally, allowing faster access with even greater privacy.
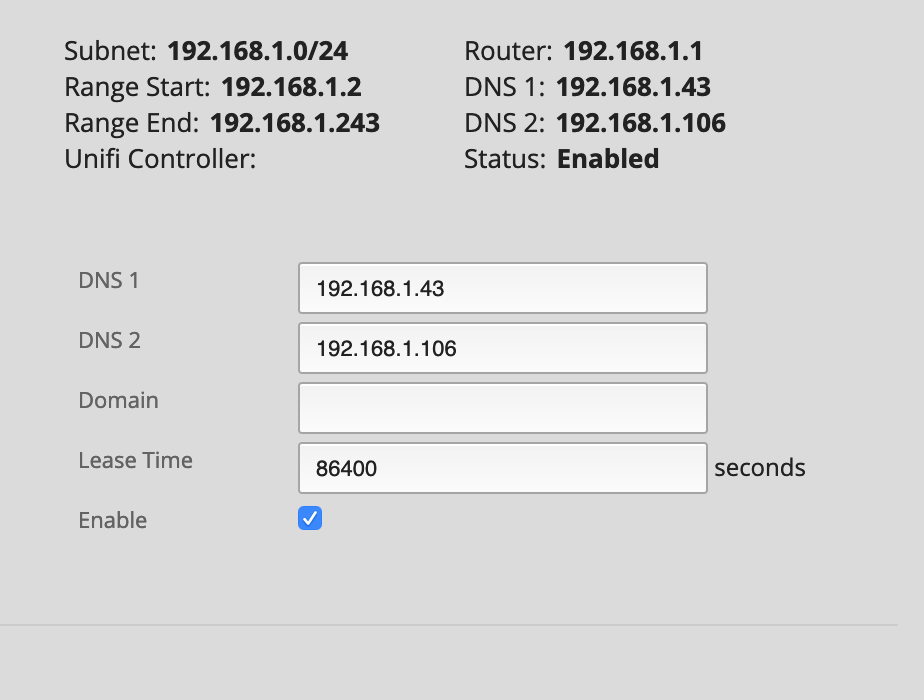
The next step is to assign the Raspberry Pi a static IP address via the network router (in this case, I made the Pi's Ethernet and Wi-Fi addresses static). This is important because we need the DNS server to have a stable IP address. Then, in the router settings DHCP settings, set the default DNS servers to those static IP addresses for the PiHole. I use the ethernet IP as the primary DNS, and it's Wi-Fi IP as the alternate DNS (in case there is an unexpected issue with the ethernet connection). After a few hours when DNS leases are renewed, clients will begin using the PiHole for DNS.
So what do the results look like?
It is generally pretty quiet when I am away from home, but when I begin using devices and browsing the web, the number of queries increases dramatically.

Queries were primarily forwarded, but a small, but growing cache and blocklist (almost 40% of total queries) improves privacy and performance.
Interestingly, a large portion of those blocked domains are not ads, but actually telematics data from devices "phoning home". In particular, Microsoft is a major offender here, and is sending data not only from Windows devices, but also from Macs, iPads, and Android phones.
Although I designed this experiment primarily as a way to improve performance and avoid advertisements, it actually became an interesting education on exactly how much data is being generated and sent from the many devices in my home. Blocking that data gives me a little more peace of mind.








Comments